🛡 Authentication
Damoov utilizes a JWT (JSON Web Token) as the standard for authentication to access its services, commonly referred to as the Bearer token.
In our digital world, protecting data is paramount. Think of authentication as the lock to your online home. With Damoov's telematics platform, the right "keys" ensure only authorized individuals gain access. Dive into this section to grasp how our authentication process safeguards your data. Read carefully—it's your virtual security at stake!
Introduction
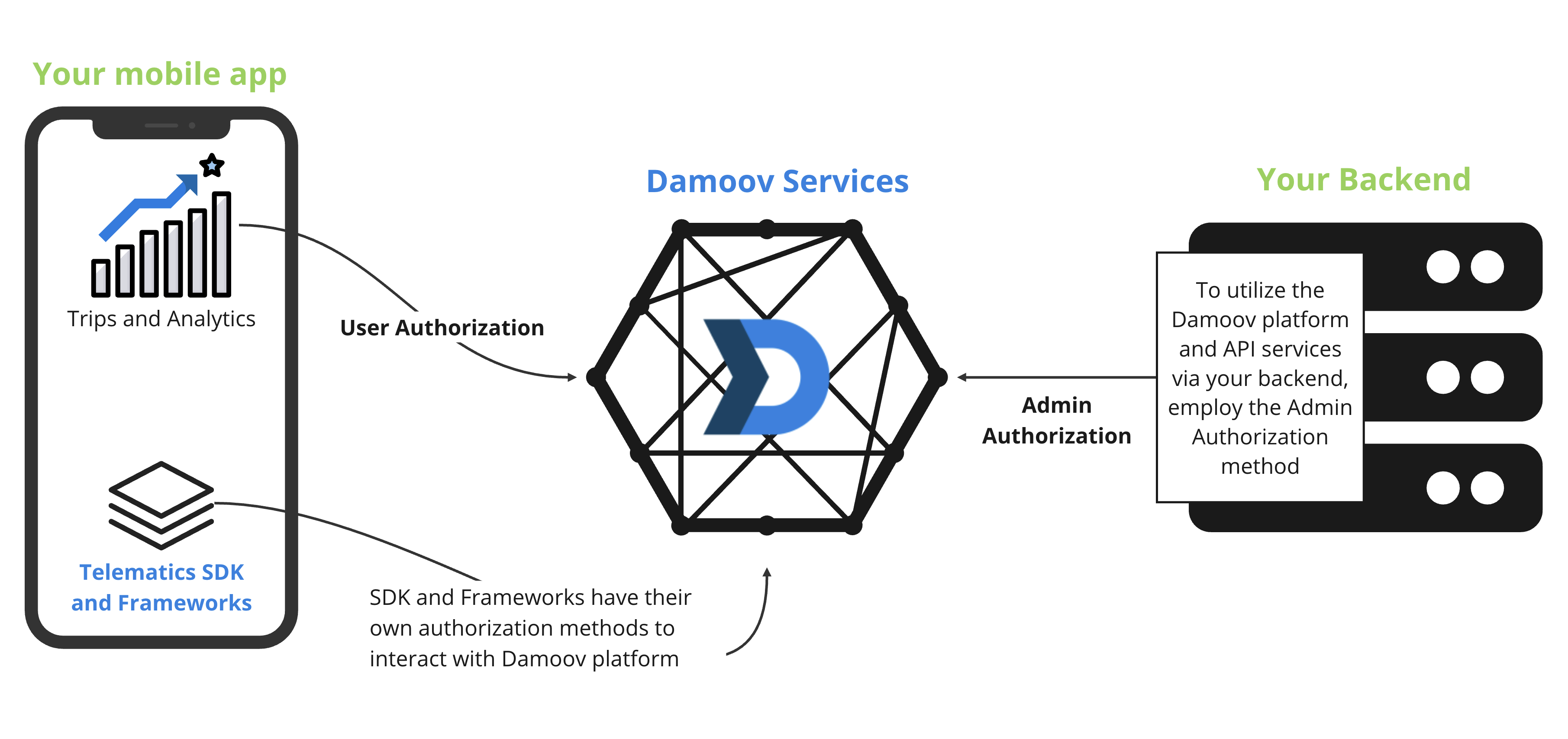
🚪 Types of Authorizations:
-
Grants access to individual user data.
-
Used to deliver analytics and trips data to the mobile application via Damoov API services.
-
Obtain the token by logging in with the user's credentials: User Authorization
-
Credentials include:
- Telematics User Id (formerly known as Device Token).
- Instance ID of the group the user is assigned to (Header).
- Instance key (Password).
- More details on user credentials can be found here.
Admin Authorization 🧑💼🖥:
- Provides developers with access to data from all users connected to their company or application account.
- Useful for backend services or when needing bulk user information.
- Obtain the token using Admin Authorization
- Admin credentials differ from Datahub login details. Retrieve admin credentials from Datahub Admin section.
⏳ Token Lifecycle:
- JWT token life cycle is 43200 seconds (120h).
- Upon expiration (401 error from API), use the refresh token to acquire a new JWT.
- JWT should be refreshed using the refresh token, which lasts for 3 months.
🚫 Note: Only use the Authorization method for the initial JWT retrieval. It has a rate limit based on the number of calls from a single IP address. Exceeding 5 calls per day results in a 429 error - Too many requests.
Token responses are structured as:
{
"Result": {
"AccessToken": {
"Token": "",
"ExpiresIn": ""
},
"RefreshToken": ""
},
"Status": 200,
"Title": "",
"Errors": []
}
⭐ Best Practices:
- For mobile applications, initiate User Authorization upon user login. Store the JWT and refresh token securely in local storage. Only refresh the JWT when it expires.
- Always communicate via HTTPS for security.
- In case of token compromise, promptly delete and regenerate credentials.
- For native app integrations, utilize the provided frameworks:
🆘 Support:
- Should you face any authentication issues, reach out to us using the Intercom bubble located at the bottom right of the screen.
Updated over 2 years ago
